Lets Cyberize India
Privacy is a right, not a feature. The way to protect privacy in this age of information technology is to develop respect for the privacy of personal information.
Confidentiality
the need to protect sensitive information while still providing access
Integrity
the processes and tools for maintaining the accuracy and trustworthiness of data
Availability
the guarantee of reliable and constant access to confidential data
A technology-first approach to knowledge and practice.
These are the different services that cyndia is providing right now.
Classification of different types of people in the virtual world
The individuals who know about cyber ethics and implement them in daily life
The individuals who know about cyber ethics but don't implement them
The individuals who are not knowing about cyber ethics and are amateurs in the cyber world
FAQ
We've got the answers
Top Cyber News
We research the news and understand the technical aspects in a user-friendly manner, so that even while reading these blogs, you tend to enjoy them but also gain new info about how things work in real life.

Weekly Unfoldings: March 03-08, 2024
Stay informed with our weekly roundup of top 10 key happenings in tech, cyber and geopolitics. Discover the most significant developments, trends and breakthroughs shaping the industry, all in one concise update. The card image tiles are designed for easy recognition of the category to which the news belongs.
Read more
Weekly Unfoldings: February 24 - March 01, 2025
Stay informed with our weekly roundup of top 10 key happenings in tech, cyber and geopolitics. Discover the most significant developments, trends and breakthroughs shaping the industry, all in one concise update. The card image tiles are designed for easy recognition of the category to which the news belongs.
Read more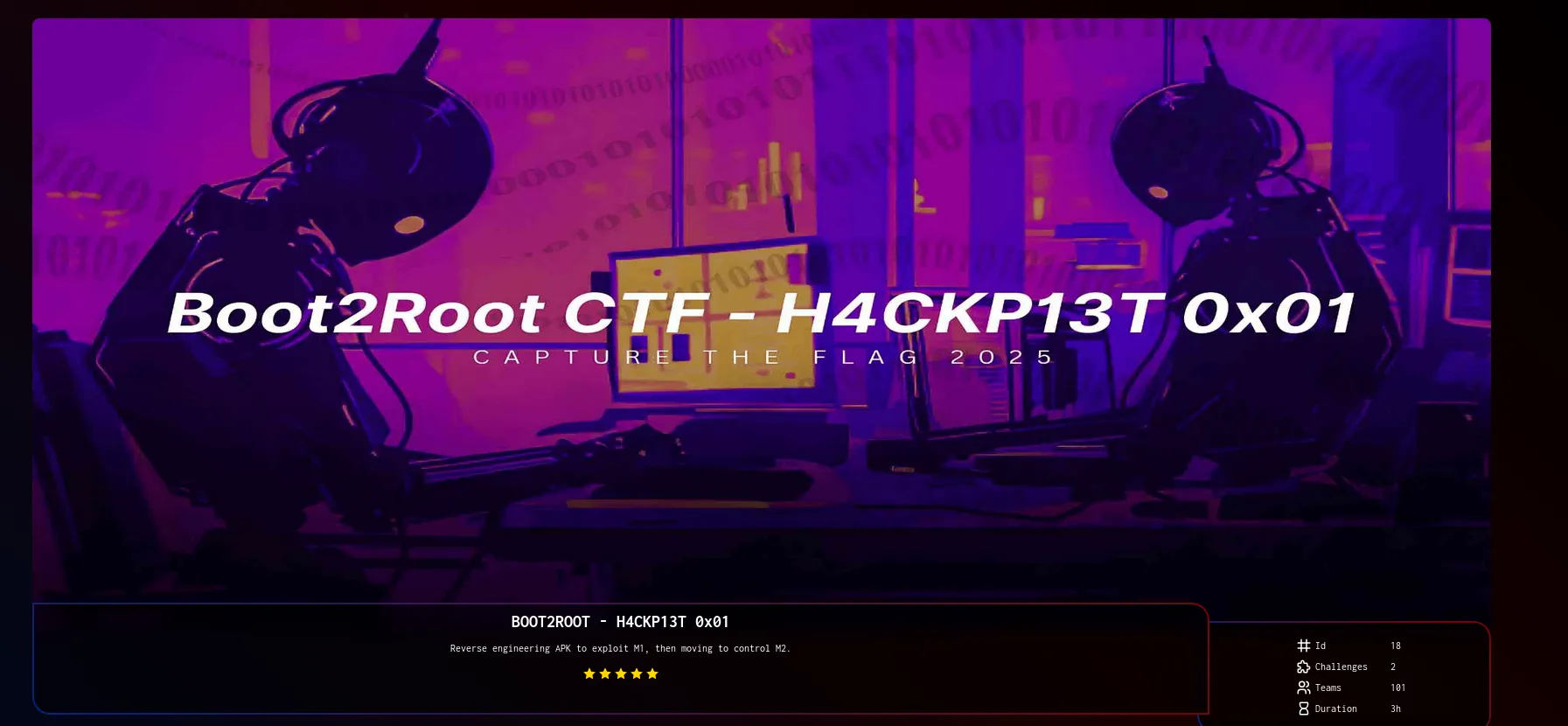
BOOT2ROOT CTF H4CKP13T 0X01
You begin with the first challenge "Exploiting Access", where your journey starts by reverse-engineering an APIC Ele. Through careful analysis, you discover crucial and hidden information that serve as the kay to exploiting the Mt system's weakne. With these insights, you successtaly breach the first machine (M1). gaining access to it. As you transion to the second challenge "Mastering Control, phase involves leveraging the foothold on Mt. extracting critical dala, and exploiting the relationship between Att and M2 to gain Having gained access to Mt, your thjective now is to move deeper by enumerating your findings which will allow you to sing to the second machine. This full control over the second machine. In summary, this CTF event challenges you to exploit vulnerabilities from an APK to compromiss the first machine and then use that access to navigate your way to the second, ultimately gaining control over both machines.
Read more

